White Hats Return $9 Million to Bridge, Giving Nomad a Break
Please note that we are not authorised to provide any investment advice. The content on this page is for information purposes only.
- Hackers returned $9 million to Nomad following the cross-chain bridge hack a day later.
- White hat or ethical hackers frequently use their expertise to find security holes in the internet.
- Nomad claims to work with law enforcement and blockchain forensics firms to identify criminals’ hackers.
The chaotic hack against the cryptocurrency bridge Nomad in August 2022. It resulted in the loss of value for the project from several different users. Using an error that was accidentally added during an update, exploiters were able to steal more than $190 million from the blockchain protocol.
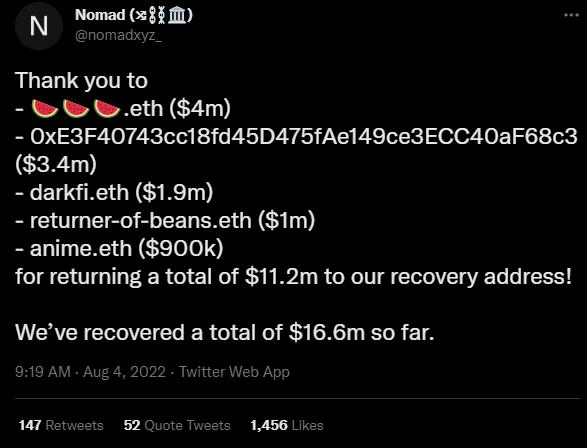
Hackers returned $9 million to Nomad following the cross-chain bridge hack a day later. According to blockchain security firm PeckShield, the amount refunded accounts for approximately 4.75 percent of the total loss. Furthermore, most recovered assets were stablecoins, with $2 million USDT and $3.8 million USDC returned by multiple addresses.
How did the breach occur?
As part of a protocol upgrade, Nomad decided to set the trusted root’s value to 0x00. Although this is standard procedure, it also aligns with the value of an Untrusted Root, giving the impression that all messages are proven. The incident was discovered through a series of transactions across the Nomad Bridge between the Moonbeam and Ethereum networks. Transactions sending 0.01 WBTC from Moonbeam to the bridge made 100 WBTC available on the Ethereum network.
After they discovered the problem, a flood of transactions took advantage of it. Even if users didn’t understand how it worked, they could still send a successful exploit transaction using their account address. As a result, the bridge’s value dropped by nearly $190 million.
How do you recognize such Hacks?
Although it appeared logical to set the initialization value of trusted roots to 0x00, doing so had unexpected consequences. However, an error during a contract update for the project enabled the Nomad Bridge attack. This hack signals the importance of performing a thorough security assessment on smart contract code before deployment. This problem can be identified using fuzzing or other testing methods in message root function validation.
Nomad Strikes Gold
White hat or ethical hackers frequently use their expertise to find security holes in the internet. In contrast to the other hackers, these white hat hackers attempted to protect Nomad cash during the impending free-for-all attack. Several people agreed to repay the money after Nomad gave them a recovery wallet.
According to PeckShield, “White Hat” hackers who protected cash on Nomad’s behalf after the hack transferred the money back to Nomad’s wallet account. Nomad revealed a wallet address for reclaiming stolen funds on August 3. According to Etherscan data, Nomad receives approximately $9 million cryptocurrency tokens as a refund.
Future Plans & Community Response
A further nine-figure bridge attack is not what the crypto industry expected right now. According to Mike Novogratz, CEO of Galaxy Digital, exuberance and arrogance have sometimes made the business appear stupid. It deters many more conservative investors when paired with massive crashes and hacks. Nonetheless, Crypto Twitter applauded the engineers and programmers who went to assist in alleviating the situation and looking for solutions to repair the flaw.
There is no question that this is another blemish on the business, highlighting the dangers of adopting alternate layer ones or layer twos. The Moonriver and Cosmos ecosystems will have suffered significantly due to this attack, and recent events show that this tendency is deteriorating rather than improving.
Those worried about their assets’ security should know the hazards of holding assets on inferior chains. The Solana controversy of the last few days has exemplified this saga pretty well, as a popular Web3 wallet seemed to have code that stole its customers’ private keys. When this is combined with Solana’s blockchain breaking quite easily when it is overloaded, transactions are frequently thrown out of the mempool. It is an excessively centralized monolithic chain, and the use case of developing dApps atop the ecosystem may be faulty.
The same argument typically applies to Ethereum’s less known competitors and those. Their chains aren’t directly hacked and often suffer from other centralization difficulties, such as the damage done to the Avalanche ecosystem when Ava Labs made a contract for $200 million in LUNA – now worth nothing.
Nomad claims to work with law enforcement and blockchain forensics firms to identify criminals’ hackers. Furthermore, the crypto bridge infrastructure has stated that it is working to correct the flaw that allowed the theft to occur in the first place.